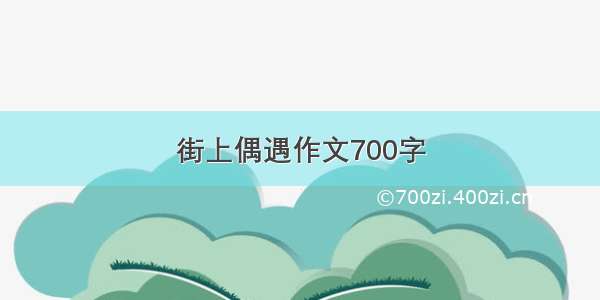
1.测试拓扑:
2.基本配置:
R1:
interface FastEthernet0/0
ip address 202.100.1.2 255.255.255.0
no shut
ASA842:
interface GigabitEthernet0
nameif inside
ip address 10.1.1.254 255.255.255.0
no shut
interface GigabitEthernet1
nameif outside
ip address 202.100.1.1 255.255.255.0
no shut
route outside 0.0.0.0 0.0.0.0 202.100.1.2
R2:
interface FastEthernet0/0
ip address 10.1.1.1 255.255.255.0
no shut
ip route 0.0.0.0 0.0.0.0 10.1.1.254
enable secret cisco
line vty 0 4
password cisco
login
-----R1开启telnet服务
PC1:
IP:10.1.1.2/24
GW:10.1.1.254
3.防火墙NAT配置:
A.动态PAT:
object network insidenet
subnet 10.1.1.0 255.255.255.0
nat (inside,outside) dynamic interface
B.静态PAT:
object network R1
host 10.1.1.1
nat (inside,outside) static interface service tcp 23 2323
4.防火墙策略配置:
A.开启ICMP审查
policy-map global_policy
class inspection_default
inspect icmp
B.允许外面Telnet内网R2
access-list outside-in extended permit tcp any object R1 eq 23
access-group outside-in in interface outside
5.测试:
A.PC1能正常通过R2内网地址telnet R2
B.R1能正常通过R2映射后公网地址telnet R1
R1#telnet 202.100.1.1 2323
Trying 202.100.1.1, 2323 ... Open
User Access Verification
Password:
R2>
C.但是PC2却无法通过R1映射后的公网地telnet R1
D.通过如下链接,修改ASA outside接口掩码为30为,PC1还是不能telnet R2的公网地址,抓包发现ASA发出tcp的syn包时,R1只是给了个ICMP重定向包。
/read.php?tid=228594
E.通过如下链接,配置hairpin NAT
/thread/2121856
①允许相同接口返回流量
same-security-traffic permit intra-interface
②定义对象和服务
object network R1-Public
host 202.100.1.1
object service telnet
service tcp destination eq 23
object service telnet-outside
service tcp destination eq 2323
③配置hairpin NAT
nat (inside,inside) source static any interface destination static R1-Public R1 service telnet-outside telnet
④测试,PC1能通过telnet 202.100.1.1 2323登录R2,登录R2后看到的源地址为防火墙内网口地址